Monitoring
Environment, building equipment, industrial sites and ITsystems, as well as utilities, need to monitor their environment and operational conditions reliably and efficiently. An overview of selected variables such as temperature, pressure, dew point, lighting level, air quality, machine operation or vibration, provide a comprehensive picture of the state of the equipment and enable the operator to respond appropriately.
Base Transceiver Station (BTS) monitoring
1-Wire
1-Wire UNI
Binary
1-Wire UNI
Binary, 1-Wire UNI
How to connect HWg WLD to a HWg-SMS-GW3 gateway
In addition to sending a SMS alert, the HWg SMS gateway can alert the recipient by dialing a call to the same number and letting it ring for a short time. This is a description how to connect HWg-WLD to the HWg-SMS-GW3. HWg-WLD detects water leaks or water floods along the entire length of the sensing cable. By placing the cable near possible flood sources, the whole area can be effectively monitored.
Energy consumption in residential buildings
Temperature monitoring in healthcare
Flood and fire detection in hotels or hostels
1-Wire
1-Wire UNI
WLD
Monitoring teploty ve zdravotnictví
Product canceled
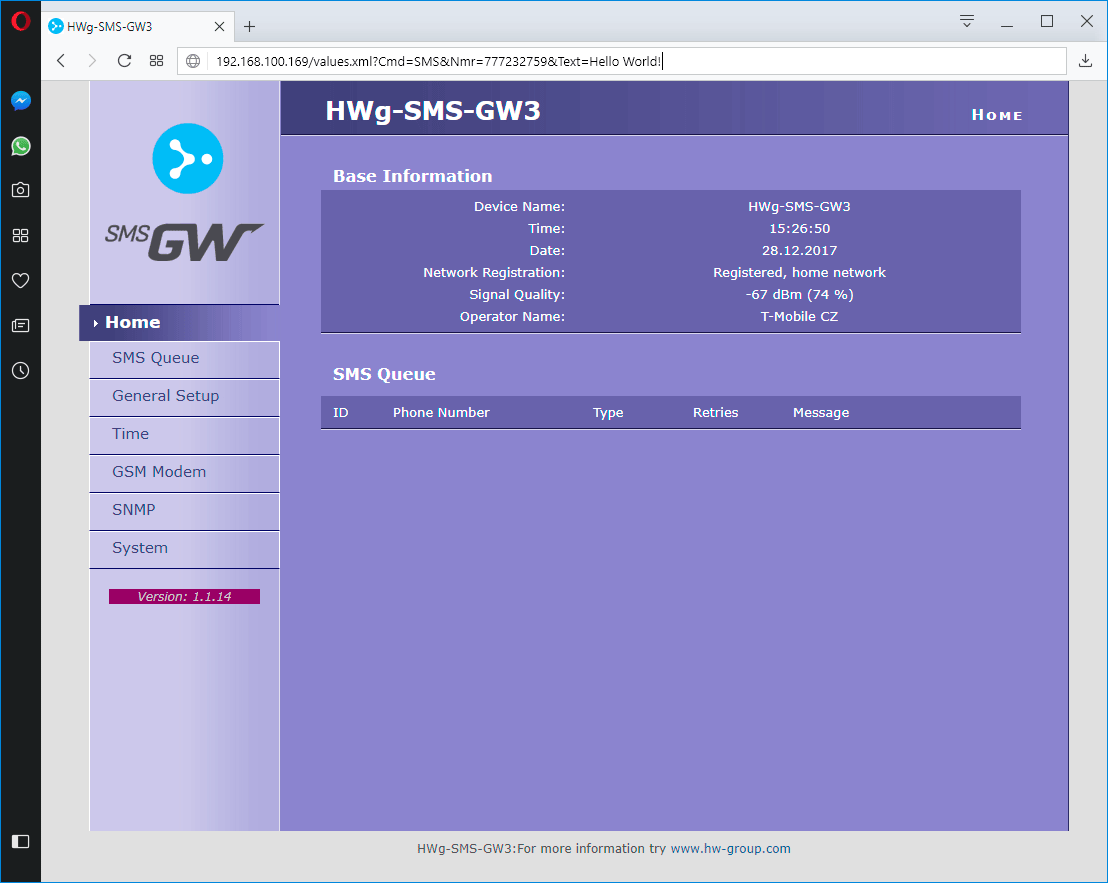
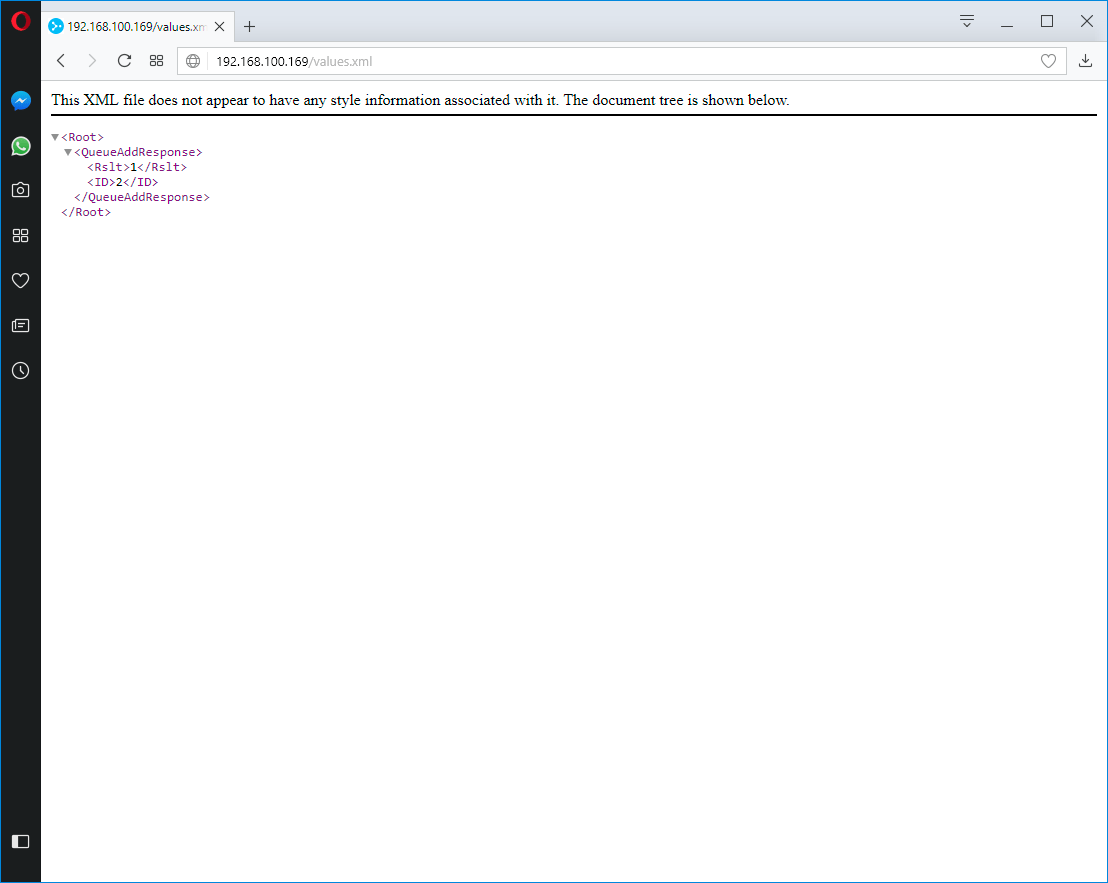
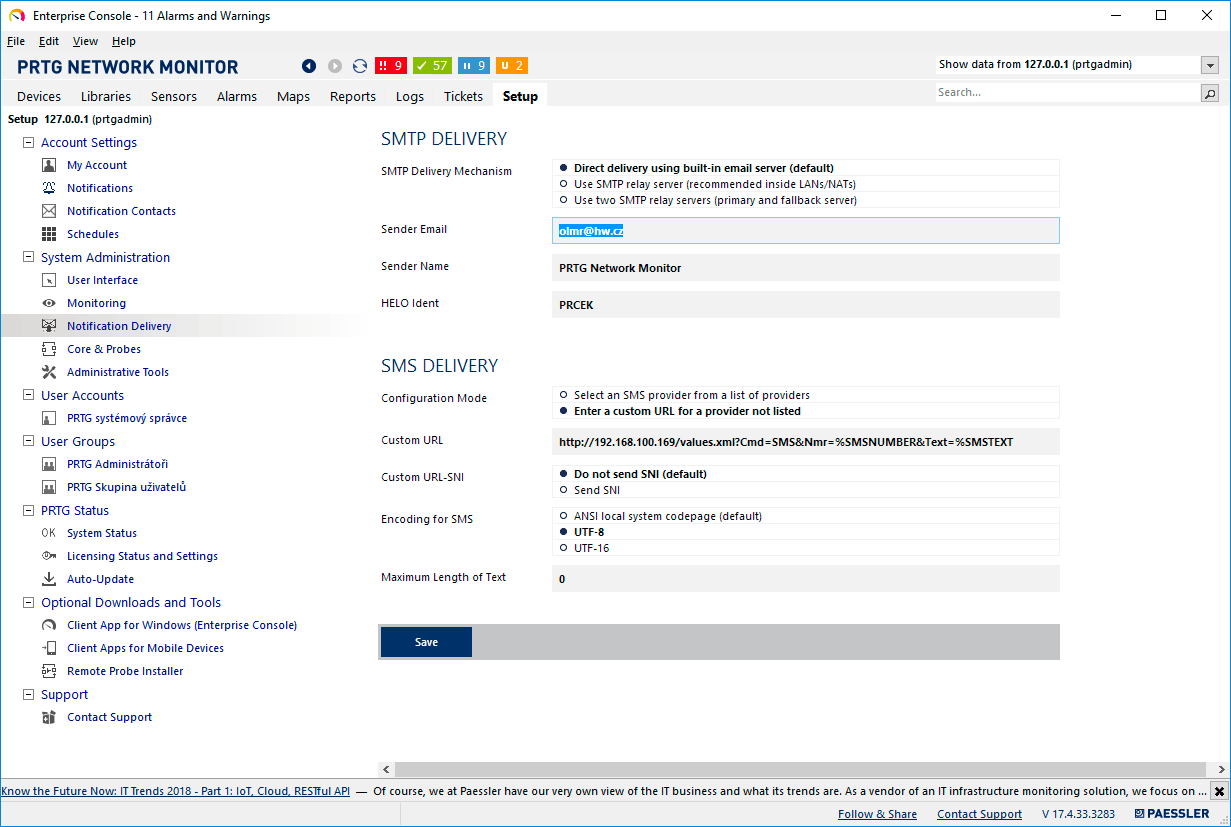
How to send SMS via HWg-SMS-GW3
HWg-SMS-GW3 is a SMS gateway for sending text message alarms over a LAN. HWg-SMS-GW3 is primarily intended for use with HW group products and software. However, its communication interfaces are sufficiently documented for use with third-party systems. This Application Note shows how to use HWg-SMS-GW3 in such third-party systems.
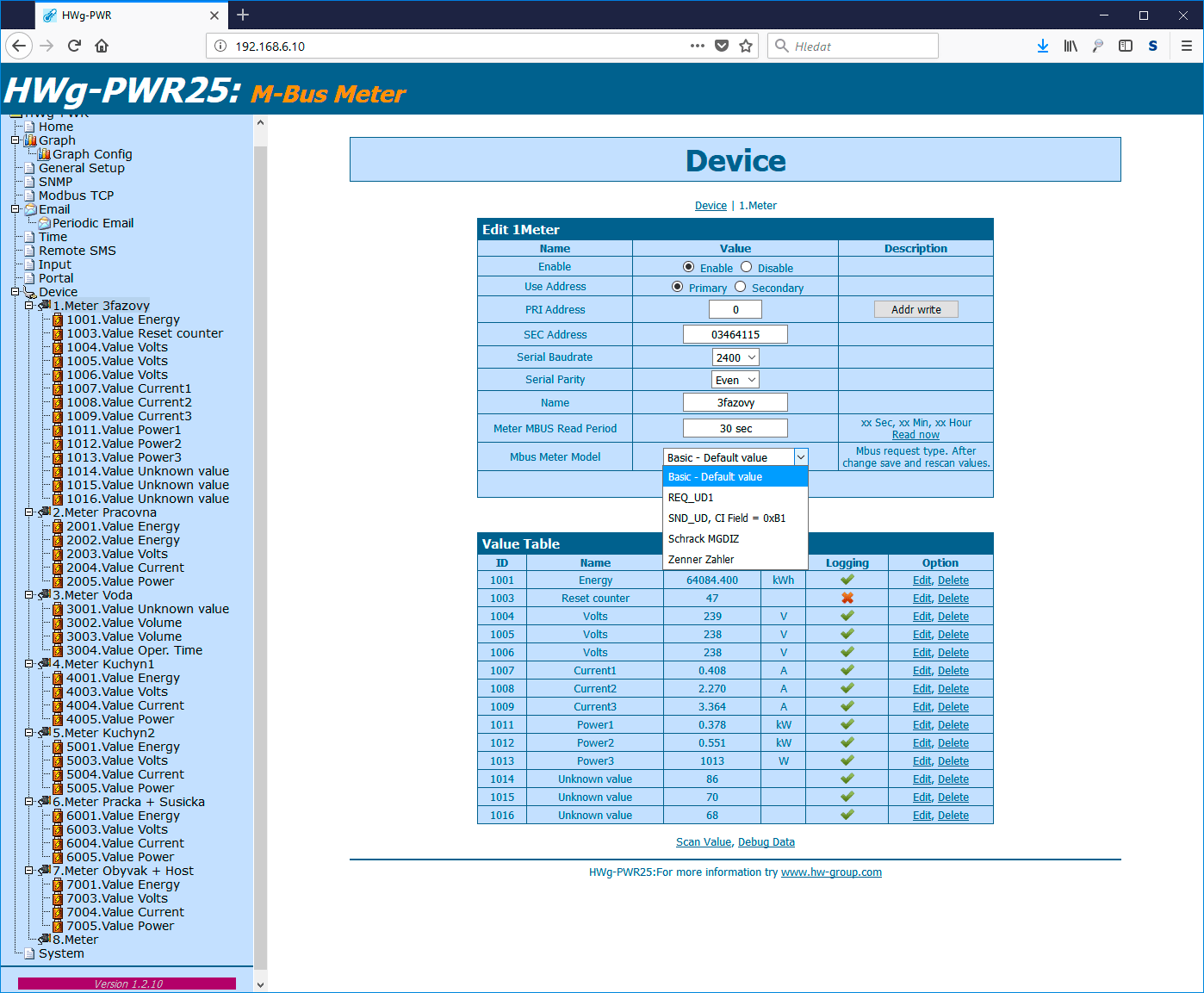
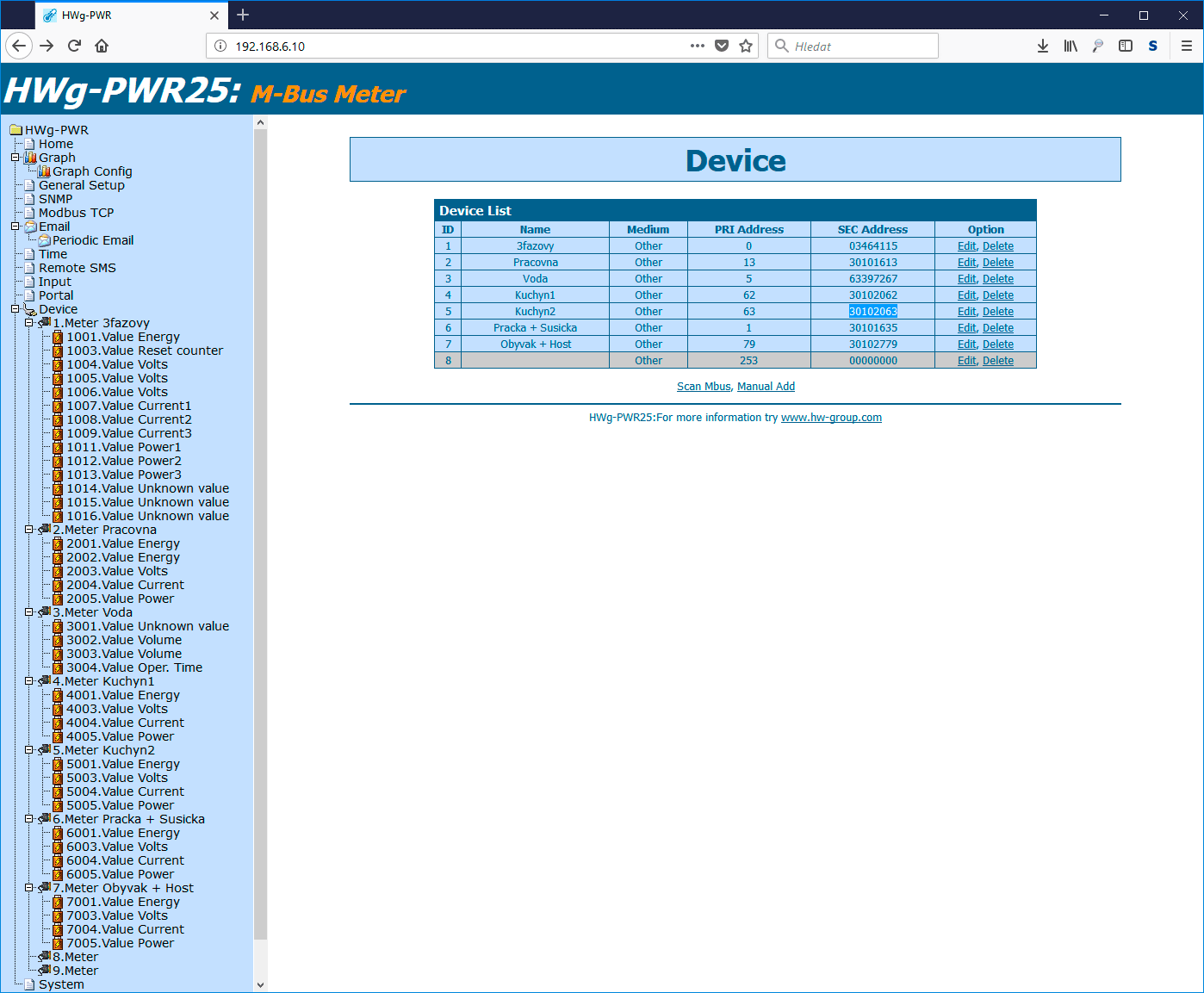
Selecting M-BUS communication type (displaying multiple values from a meter)
The M-BUS is designed for low consumption, and for this reason allows to query device values using different requests. The issue is that some meters respond to a “Basic” request only with the total consumption values; another request type (REQ_UD1, SND_OUD or other) must be used to display more readings, such as the immediate consumption, flow, etc. To this end, HWg-PWR allows to add another meter with the same secondary address. A hidden option is used to activate these advanced request settings.
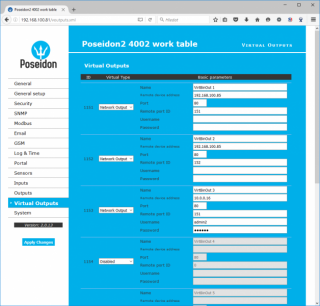
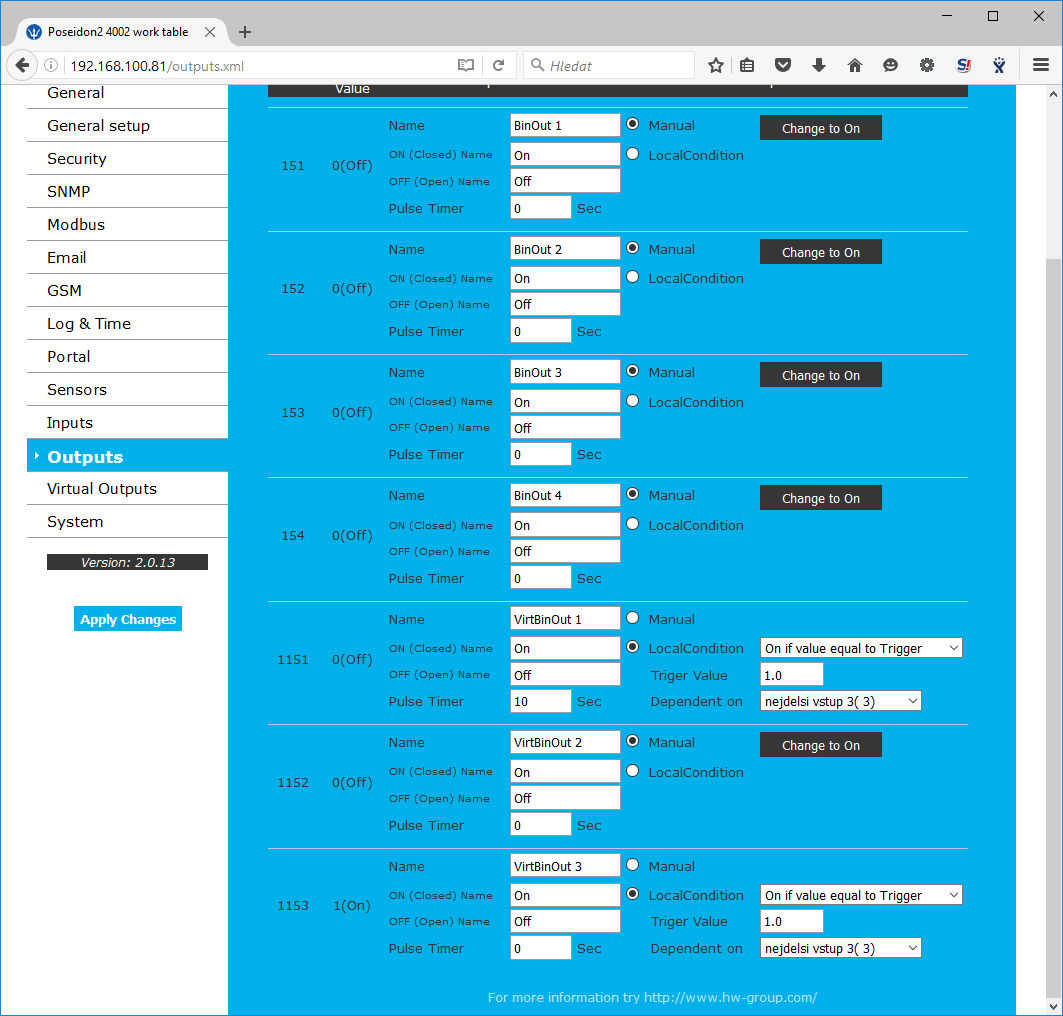
Virtual outputs in Poseidon2/Damocles2
Virtual outputs in Poseidon2 and Damocles2 units allows to use outputs from different Poseidon2 and Damocles2 units (Box2Box). De facto we are talking about similar feature, which was based on SNMP traps, only in case of Virtual outputs the communication runs more reliable way via TCP/IP protocol, it is repeated (done each 60s), secured and all functions work this way too, conditions and features same as with physical outputs.